When you turn on your MacBook, you see that something is wrong: certain files have vanished, while others have been added. You start to wonder if your computer has been watched.
So, how can you determine if someone is accessing your MacBook remotely? Check your logs to ensure that no new users have been created, that remote login, screen sharing, and remote management have been blocked, and that no spyware is installed on your machine.
What is remote access, and how does one set it up on a MacBook?
Allowing remote logins from another computer, enabling Screen Sharing, or allowing access via Remote Desktop are the three options for remote access to macOS.
Both methods are legal, but if you don’t recall using any of them, you’ll need to know how to switch them on and off.
Remote login to macOS
Secure Shell can be used to log in to your Mac on computers that run the macOS operating system (SSH).
The following are the steps to enable remote login:
Select System Preferences from the drop-down menu. You may get there by selecting the apple icon in the top bar on the left. After clicking the Apple icon, a drop-down menu will appear, from which you should select the System Preferences menu item.
Double-click the Sharing folder to open it. On the left, select the Remote Login checkbox.
You now have the option of granting access to all users or specific users.
Users with access can use SSH to log in and read your computer’s contents after Remote Login is enabled.
Access to Mac screen using Screen Sharing
You can activate Screen Sharing if you need assistance from IT to make modifications to your MacBook, or if you’re working on a project with others and want to share your screen. The following are the steps to enable:
- Select System Preferences from the drop-down menu.
- Double-click the Sharing folder to open it. On the left, select the Screen Sharing checkbox.
- Allow access to either all users or a subset of users.
Start the Screen Sharing programme on another Mac (from which you want to access your Mac).
It can be started by pressing the Command and Space keys at the same time. Type Sharing into a popup form and press Enter. Fill in your computer’s name. I had to type in “dev-pros-MacBook-Pro.local” in my case.
A new window showing the shared screen of another machine will appear. You can now control the display.
Remote Desktop with Remote Management
Finally, activating Remote Desktop allows you to log into a machine running macOS.
The following are the steps to enable:
- Select System Preferences from the drop-down menu.
- Double-click the Sharing folder to open it. On the left, select the Remote Management check box.
- Allow access to either all users or a subset of users.
- There will be many Sharing options where you may fine-tune the type of access you want to grant, such as observing, changing settings, deleting, copying, and even restarting the computer.
Now you can use Apple Remote Desktop to access this Mac – it’s a $79.99 programme available from the Apple Store at the time of writing.
If your Mac is being watched, this graphic (two rectangles) will appear near your computer time in the top right-hand corner:
You’ll be able to know if you’re being watched when that icon shows. By selecting the Disconnect option, you can also disconnect the viewer:
You can also open the Sharing folder in System Preferences by clicking “Open Sharing Preferences…”.
Since your query was about someone remotely accessing your computer, it’s unlikely that you’ll require any of the above-mentioned sharing capabilities.
In this situation, make sure that no one is authorised to access the Sharing folder under System Preferences by checking all choices and unchecking all others.
How To Tell If Your Mac Was Hacked
The first step in determining whether your Mac was hacked or not is to see if screen sharing or remote management was enabled and if your screen was being viewed.
There are a few other locations to look, which I’ve listed below.
Four Signs That Your Mac Has Been Hacked
If you’re reading this, you’ve probably noticed something strange going on with your Mac.
You may have a hunch yet be unable to describe it. Most of those indicators, however, can be explained by factors other than malware or hackers.
So, let’s have a look at the most important indicators.
Mac suddenly became slow for no apparent reasons
Some of the reasons why a Mac can be slow are as follows:
- There is a virus or other malware on your computer.
- On a Mac, there isn’t enough disc space.
- A new operating system was installed.
- Failure of the hardware
Mac is using more Internet than usual
This one is harder to notice now than before because Mac is utilising more Internet than normal.
We used to be able to use only a certain amount of Internet bandwidth. Many individuals today have limitless cable data, so you may not even be aware that something is going on.
If you’re on a limited plan and your data use has increased significantly (by more than 25%), it’s time to look into it.
The following could be the reasons:
- Hackers are using your Mac as a bot.
- There is a virus or other malware on your computer.
- Your child has grown up and now spends all day on your computer watching YouTube.
- Someone is eavesdropping on your Wi-Fi (read more below)
Problems with the Internet, like the previous symptom, could indicate that the browser is infected with a virus or adware.
It could also be a recent browser upgrade. Alternatively, the system could have become unstable.
Programs crashing more often
Have you noticed how some apps become stuck and eventually crash?
It’s usually an indicator of malware.
The following are some more causes of frequent app crashes:
- Memory lapses (RAM)
- Insufficient disc space
- Unstable system for a short time
- Failure of the hardware
- Browser pop-ups that are unusual
This is something that we’ve all witnessed. You download an app from the Internet that appears to be legitimate software. But you had no idea that an excellent app came with bloatware.
The outcome is usually a change in your default search engine from Google to Yahoo, a change in your home page, and new symbols in your browser toolbar.
However, there may be additional problems, such as adware.
Adware is attempting to divert you to sites that are unrelated to your search.
Their purpose is to send people to specific websites. They make more money when there is more traffic. As a result, they bombard your screen with pop-ups in the hopes that you would click and visit the site you don’t want.
New files appear or old files disappear
Malware frequently generates new files with obscure names. Ransomware, for example, encrypts and renames your contents on your hard drive. There could, however, be more harmless answers.
For example, just because you can’t find a file doesn’t indicate it was erased by malware or someone who accessed your computer remotely. Perhaps you simply cannot recall deleting the file or folder. Check Trash on Mac first in this scenario.
If you’re still having trouble finding what you’re looking for, take a look at my post on how to locate any files. If the file is still on your Mac after reading my post, I guarantee you’ll be able to find it.
Remove False Positives from the equation.
While you may suspect anything is wrong with your computer, it could very well be a routine occurrence.
Before you start freaking out, try these things:
Reboot
Software flaws might render your system’s current state unstable at times. Many issues can still be solved with a reboot. You have the option of restarting or shutting down and restarting. The result will be identical.
NVRAM/PRAM reset
Many Mac peripherals require setup information, which is stored on a small memory chip in Macs. Surprisingly, this area is prone to corruption.
Fortunately, resetting the NVRAM/PRAM and SMC is a straightforward remedy.
Apple provides excellent instructions for doing these procedures.
What they don’t tell you is that a fix will only work if you reset 2-3 times in a row. This is something I learned through the school of hard knocks so you don’t have to.
Clear some space on disk
Program delay, app crashes, high CPU utilisation, and MacBook overheating can all be caused by a lack of space on your startup disc. This may cause you to believe that your Mac has been hacked.
So, first, see how much space you still have. And if that isn’t enough, you may either invest money on disc cleaning software or read my post on free disc cleaning tips:
New operating system
Every year, Apple releases a new version of macOS. Bugs still happen, even when they do everything they can to build high-quality software.
My podcast app, for example, now freezes every time I pause after the recent iOS upgrade on my iPhone. I’m still stumped as to why this is happening because I’m too busy.
In the case of the current issue, if you recently installed an OS update, take some time to see if the troubles you’re experiencing are common for the release.
Look for signs of hardware failure.
Macs are quite dependable and can last for years.
Any gear, though, will eventually fail. Unexpected app crashes, for example, can be caused by a failing disc. The machine will not start if the RAM fails.
On the Apple website, there is a decent article about running hardware diagnostics. Try to figure out what it will say.
Examine Your Mac For Keyloggers (Legal And Malware)
For a long time, I believed that recording keyboard strokes was all that keyloggers could do.
Imagine my surprise when I started writing about keyloggers.
Let’s say you’re still suspicious that your computer is infected with spyware.
In that situation, you can use a third-party programme like Little Snitch, which monitors applications and uses advanced rules to restrict or allow them to access to connected networks.
Setting up the regulations for Little Snitch, on the other hand, might be difficult.
A keystroke logger, sometimes known as a keylogger, is a common spyware tool. Keyloggers used to be simple programmes that recorded the characters you typed on your keyboard, but they’ve evolved dramatically in recent years.
Keyloggers, for example, can snap screenshots every 30 seconds or track your chat activities, including messages sent to you.
Because keyloggers are easier to install and have more powerful functions, I feel they pose a far higher security risk.
Here’s a link to an essay I wrote regarding keyloggers:
Verify If New User Accounts Have Been Added
Remote login and sharing options, as we’ve seen, necessitate granting access roles to local users.
If your system has been hacked, the hacker is extremely likely to have added a new user to gain access to it. Perform the following procedures on macOS to find all users:
- Start the Terminal app by pressing Command and Space and typing Terminal in the pop-up box, or by heading to Applications and then the Utilities folder.
- Type dscl. list /Users | grep -v ‘_’ in the Terminal window.
It listed macmyths, nobody, root, and daemon on my laptop. My current user is Macmyths, and the rest are system accounts.
If you notice accounts you don’t recognise, they were most likely established by a hacker.
Type the following command into the Terminal to see when all user accounts were last used:
last
MacOS will keep track of the times and dates of each account’s logins. If any of the accounts were accessed at an unusual time, it’s probable that a hacker logged in using a genuine account.
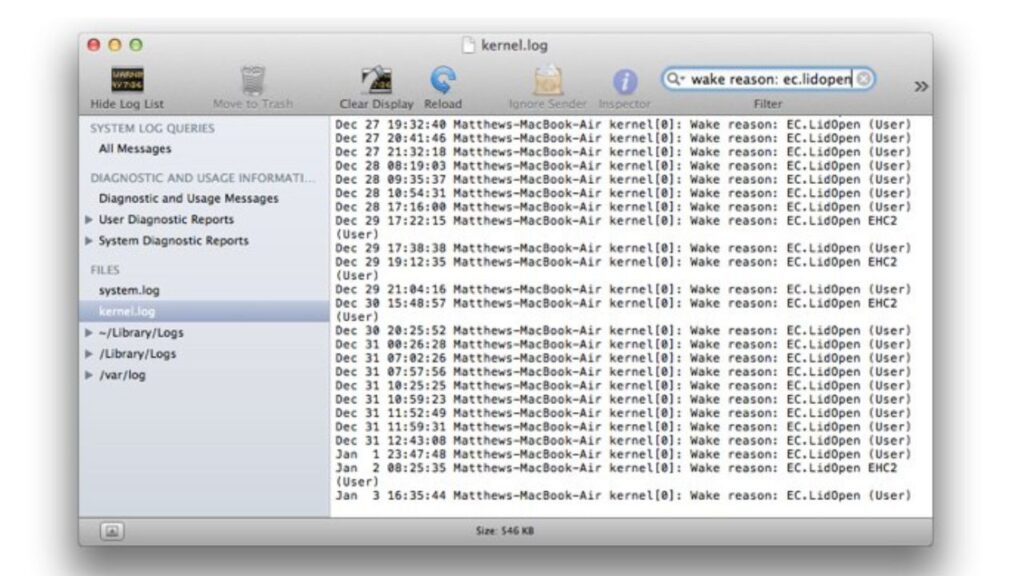
Check The Logs For Possible Access Issues
Checking the system logs for any probable access concerns may be beneficial.
To locate a system log, select Go from the top menu or press Shift, Command, and G at the same time. Type /var/log into the “Go to Folder” pop-up and press Enter.
Now you must locate the system.
Search for word sharing in the log file.
I discovered the following screen sharing log entries, for example:
For instance, I found the following screen sharing log entries:
Mar 24 12:31:03 dev-pros-MBP com.apple.preferences.sharing.remoteservice [84412]: DEPRECATED USE in libdispatch client: dispatch source activated with no event handler set; set a breakpoint on _dispatch_bug_deprecated to debugMar 24 12:31:05 dev-pros-MBP com.apple.xpc.launchd1: com.apple.screensharing (lint) : The HideUntilCheckIn property is an architectural performance issue. Please transition away from it.Mar 24 12:31:05 dev-pros-MBP com.apple.xpc.launchd1: Unknown key for string: SHAuthorizationRightMar 24 12:31:26 dev-pros-MBP com.apple.xpc.launchd1: Endpoint has been activated through legacy launch(3) APIs. Please switch to XPC or bootstrap_check_in(): com.apple.screensharing.serverThese were log entries when someone logged in to my system remotely:
Mar 24 12:39:30 dev-pros-MBP com.apple.xpc.launchd1: Unknown key for string: SHAuthorizationRightMar 24 12:40:50 dev-pros-MBP com.apple.xpc.launchd1: Service exited due to SIGKILL | sent by com.apple.preferences.sharing.re[84529]Verify Home Wi-Fi Was Not Hacked
You don’t have to be concerned about your computer alone.
The data passes through the Wi-Fi router before entering the system. Furthermore, bad guys have the ability to read any internet traffic, including emails and online transactions.
Check Which Programs Have Access To Camera And Mic
These are only two of the emails I received in the past month:
Email 1:”A few days ago, I received an extortion email from y…[email protected] threatening to reveal webcam video’s photographs of my wife and me in our private lives.” There are a few things I can check to see whether my computer’s webcam being controlled from outside?”
Email 2: “I believe my MAC (I have a Macbook Pro) has been hacked, yet all of my software is up to date.” Someone sent me an email claiming that they had recorded anything on my MacBook camera. What is the best way for me to see if this is possible?”
I’m guessing you have at least two queries after reading these emails:
- Is it feasible for someone to record what I’m recording on my camera?
- How can I tell whether I’ve been recorded?
To begin with, you can record your camera from a distance.
It’s actually quite simple.
If a hacker gains access to your Mac, all he has to do is open a Quick Time Player (or Facetime) and begin recording a new movie.
Other apps that can record the camera while being hidden are, of course, available.
A green light will appear next to the camera if someone is recording you with a MacBook camera.
The green camera may light up even if no recording is taking place because a programme has gained access to the device. However, recording is impossible without the green signal turned off.
However, if you were not paying attention at the time of recording (either because you were busy or because you were not near the computer), you will never be able to tell if you were captured definitively after the fact.
You could use the lsof command with the Terminal on earlier versions of the Mac operating system, like follows:
lsof | grep -i "AppleCamera"However, this command has recently stopped being functional.
Rather than reading Apple logs, use MicroSnitch to see if your camera or microphone is active.
This is a pretty useful little tool. It shows in the menu bar of your Mac once it has been started, and its icon changes if either video or audio, or both, becomes active.
The Microsnitch log file is another great function. You could check the log for previous device activity if you spotted any unusual activity.
It’s available for download on their website or in the Apple App Store.
Go to System Preferences -> Security and Privacy for another option.
Check programmes under the Camera and Microphone portions of the Privacy tab. Remove any programmes that you are unfamiliar with (you can always add them back if needed).
Finally, if you feel that someone is controlling your laptop and that they may be viewing you through the webcam, immediately cover the webcam with a cover.
Check Which Programs Run On Start
Check to see which programmes start automatically when you turn on your computer.
Check one more thing while you’re in System Preferences.
Select the user from the Users and Groups icon, then click the Login Items tab.
Take out anything you don’t recognise.
Warning: Before uninstalling an application, look it up on the internet first. You don’t want to break the apps you rely on, do you?
Install And Run Antimalware Program
I recently contacted Apple Support to express my dissatisfaction with the performance of my MacBook Pro.
I could have fixed the problem myself, but I was curious how much it would cost Apple to diagnose a 5-year-old MacBook.
I expected them to charge me something because I don’t have AppleCare for my Mac.
They didn’t charge anything, which is a spoiler.
When I contacted, the Apple representative told me that the first thing I needed to do was download the Malwarebytes app.
Malwarebytes is a good option for malware scanning, but it isn’t the best. The same can be said about Avast’s free edition.
In fact, following a recent test, I have stopped recommending it to any Mac user.
I put a dozen antimalware programmes to the test, and only one of them caught 100 percent of the 117 malware samples I downloaded on my MacBook.
So, if you’re looking for a good antivirus for Mac, go no further.
Set Up Traps Against Hackers
If you fear your computer has been hacked, I found a neat and free tool that may be used to set traps. Canary tokens are what they’re called.
When a potential hacker accesses an email or document containing the token, it sets off a remote event. After that, you’ll receive an email notification.
Here’s where you can learn more about security alerts.
What comes next?
I’ve been getting emails from my readers on a regular basis since I started my blog in 2019. The bulk of emails fall into two categories, which is interesting to note:
How can I keep my Mac safe from hackers?
Should I get a MacBook Pro or a MacBook Air?
I had started responding to individual emails, but as the quantity of emails continued to rise, I found myself unable to assist everyone. After all, I have a full-time job and a family to support.
As a result, I decided to write a series of articles about various security topics, putting what I know in one place so that everyone may find answers to their queries.
All Mac security articles have been grouped together, and the best way to keep track of them is to click the Next button at the bottom of each post.
It will take some time (about 30 minutes), but you will end up knowing more about Mac security than the majority of non-technical people.