It is important to keep up with the most critical security issues and vulnerabilities when running a web site. In reality, all web applications are susceptible to anything. Knowing which vulnerabilities are the most exploited and how risk management will enable you to protect your web application.
What is OWASP?
An international, not-for-profit organization dedicated to web application protection is the Open Web Application Security Project or OWASP. An online community that publishes web application security researches. One of the fundamental concepts of OWASP is that their resources are freely available on their websites so that anyone can enhance their protection on their own web applications.
What is the OWASP Top 10?
The OWASP considers the top 10 a ‘list of importance,’ and suggests that all organizations use the report in their processes to reduce security risks. OWASP Top 10 is the list of the 10 most common application vulnerabilities.
Top 10 OWASP Vulnerabilities in 2020 are:
1. Injection
The attacker sends invalid data through input or some other data submission to the website client, this is when the code injection takes place.
Check out: SQL injection cheat sheet
One Most common example around this security vulnerability is the SQL query consuming untrusted data. You can see one of OWASP’s examples below:
String query = “SELECT * FROM accounts WHERE custID = ‘” + request.getParameter(“id”) + “‘”;
By calling up the web page executing it can be exploited easily.
http://example.com/app/accountView?id=’ or ‘1’=’1
causing the return of all the rows stored on the database table.
Validation and/or sanitization of data submitted by users will avoid injection attacks. (Validation means the denial of questionable data while sanitizing the cleanup of suspicious data bits)
2. Broken Authentication
Authentication (login) system vulnerabilities allow attackers to access user accounts and even to access an entire system with administrative rights. Websites with vulnerabilities to broken authentication are very common on the Internet.
Avoid making the login page for administrations open to all users of the website to reduce broken authentication risks:
- /administrator on Joomla!,
- /wp-admin/ on WordPress,
- /index.php/admin on Magento,
- /user/login on Drupal.
In certain cases, two-way authentication (2FA) and repeated attempts to login are required to mitigate authentication vulnerabilities.
3. Sensitive Data Exposure
If web applications don’t protect sensitive data such as
- Credentials
- Credit card numbers
- Social Security Numbers
- Medical information
- Personally identifiable information (PII)
- Other personal information
Attackers may access and use it for that data for adverse purposes. The risk of data leakage can be reduced if all sensitive data are encrypted and caching(Caching is the process of re-use data temporarily) sensitive information is disabled.
4. XML External Entities (XEE)
It’s an attack on an XML input web program. Such knowledge may apply to an external party that tries to take advantage of a flaw in the parser. This arises when a weakly designed XML parser processes XML input containing a reference to an external entity.
XEE Attack Vectors
- Vulnerable XML Processors
- Vulnerable code
- Vulnerable dependencies
- Vulnerable integrations
Websites that support a less complicated data form such as JSON, or at least patch XML parsers and disable the use of external entities within an application XML, are the best ways to avoid XEE attacks.
5. Broken Access Control
In the protection of the website, access control means restricting the parts or pages that visitors can enter in compliance with their requirements. Controls for broken access allow attackers to bypass permissions and perform tasks as privileged users, such as administrators.
Examples of Broken Access Control
Here are some examples of what we consider to be “access”:
- Access to a hosting control / administrative panel
- Access to a server via FTP / SFTP / SSH
- Access to a website’s administrative panel
- Access to other applications on your server
- Access to a database
Attackers can exploit authorization flaws to the following:
- Access unauthorized functionality and/or data
- View sensitive files
- Change access rights
Access controls can be protected by the use and strict monitoring of authorisation tokens * by a web application.
6. Security Misconfiguration
The most common security flaw in the list is security misconfiguration and is mostly the product of default configurations. Today’s CMS systems can be daunting from a security point of view. The most common attacks are by far fully automated. Many of those attacks are based on the default configuration of users.
Most Commons are:
- Unpatched Flaws
- Default configurations
- Unused pages
- Unprotected files and directories
- Unnecessary services
It can be minimized by eliminating redundant application features and ensuring error messages are more general.
7. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS), which affects many web-based applications, is a commonly used vulnerability. XSS attacks include the implementation of malicious client scripts on the website as a propagation tool. The dangers of XSS are that they allow an attacker to insert code into a website and change the display, forcing the browser of a victim to execute the code that the attacker gives when loading the website.
Cross-site scripting can be eliminated by escaping untrusted HTTP requests and validating and/or content created by users. Using modern web development frameworks such as ReactJS and Ruby on Rails, you can also secure cross-site scripting.
Check Also: Magento SEO Tips to Get Organic Traffic
8. Insecure Deserialization
Serialization involves taking and transforming objects from the Computer Code into a format that can be used for a particular purpose, like storing or streaming data on a disk. Deserialization is the other way round: translating serialized data into objects which can be used by the application.
The unpredictable manipulation of deserialization is the result of the deserializing of data from undesirable sources that may lead to severe impacts such as DDoS attacks and remote code execution attacks.
It is best not to accept serialized objects from untrusted sources to protect your web application from this form of danger.
9. Using Components With Known Vulnerabilities
All should understand that the lack of upgrading every piece of website software would inevitably contribute to significant security threats sooner rather than later. Thousands of websites make use of some of the most common components; a security flaw in one of these components may make the websites vulnerable to being exploited.
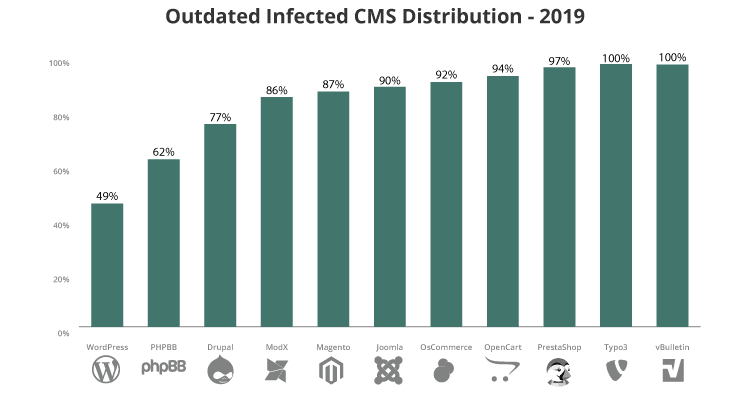
In order to reduce the risk of running components that have known vulnerability, developers should exclude unused parts from their projects, and ensure that components are obtained from a trustworthy source and are up to date.
10. Insufficient Logging And Monitoring
Most web applications may not take appropriate measures to identify data breaches. The average time it takes to discover a violation is about 200 days. Without effective logging and tracking, harm to a website compromise will increase.
OWASP suggests that web developers should implement logging and tracking and incident response plans so that their systems are aware of attacks.