AnyDesk, a popular remote desktop software, confirmed on Friday that it suffered a cyberattack that allowed hackers to access its production systems. The company said it has taken immediate steps to secure its systems and protect its customers. However, the incident raises security concerns for the users of AnyDesk, who may be vulnerable to potential data breaches.
AnyDesk Cyberattack and Password Reset
AnyDesk became aware of the cyberattack after discovering unusual signs of intrusion on its product servers. The company conducted a security audit and activated a remediation and response plan involving cybersecurity experts CrowdStrike. The company also notified the relevant authorities and is working closely with them.
According to sources, the hackers stole source code and code signing certificates during the attack. Code signing certificates are employed to authenticate and ensure the integrity of software. If compromised, they could allow attackers to distribute malicious software under the guise of legitimate applications.
AnyDesk said it has revoked all security-related certificates and replaced them with new ones. It also said it has improved or replaced the systems that were affected by the attack. The company clarified that the incident was not a ransomware attack and that it has no evidence that any end-user devices have been affected.
As a precaution, AnyDesk has revoked all passwords to its web portal, my.anydesk.com, and recommended that users change their passwords if they have reused them on other websites. It also urged users to use the latest version of AnyDesk with the new code signing certificate.
Impact and Repercussions
The cyberattack on AnyDesk poses serious security risks for its customers, who use the software to remotely access their personal computers and other devices. AnyDesk has over 170,000 customers, including Amedes, AutoForm Engineering, Comcast, LG Electronics, 7-Eleven, Samsung Electronics, Spidercam, MIT, NVIDIA, Siemens, Thales, and more.
If the hackers were able to access the session authentication tokens or the device fingerprints of the users, they could potentially hijack their remote connections and access their data. This could lead to data theft, identity fraud, ransomware, or other malicious activities.
AnyDesk said it has designed its systems in a way that session authentication tokens cannot be stolen and that they are associated with the device fingerprint. The company said it has no indication of session hijacking as to its knowledge this is not possible. However, users should still be cautious and monitor their devices for any suspicious activity.
The cyberattack on AnyDesk also highlights the importance of securing remote desktop software, which has become more widely used due to the COVID-19 pandemic and the shift to remote work. Remote desktop software enables users to access their devices from anywhere, but it also exposes them to potential cyberattacks if not properly secured.
Users should always use strong and unique passwords for their remote desktop software and web portals, and enable two-factor authentication if possible. They should also keep their software updated and use reputable antivirus and firewall software to protect their devices. They should also avoid clicking on any links or attachments from unknown sources, and report any suspicious or unauthorized activity to their service providers.
New Update Resealed By AnyDesk
In response to the recent security breach that compromised its production servers and led to the theft of source code and code signing keys, AnyDesk has swiftly taken action. The company has released a new update, version 8.0.8, aimed at addressing the vulnerabilities exposed during the cyberattack.
BleepingComputer examined earlier iterations of the software, and the outdated executable files were authenticated using the name ‘philandro Software GmbH’ with the serial number 0dbf152deaf0b981a8a938d53f769db8. The updated edition is currently endorsed by ‘AnyDesk Software GmbH,’ accompanied by a unique identifier of 0a8177fcd8936a91b5e0eddf995b0ba5, as depicted below.
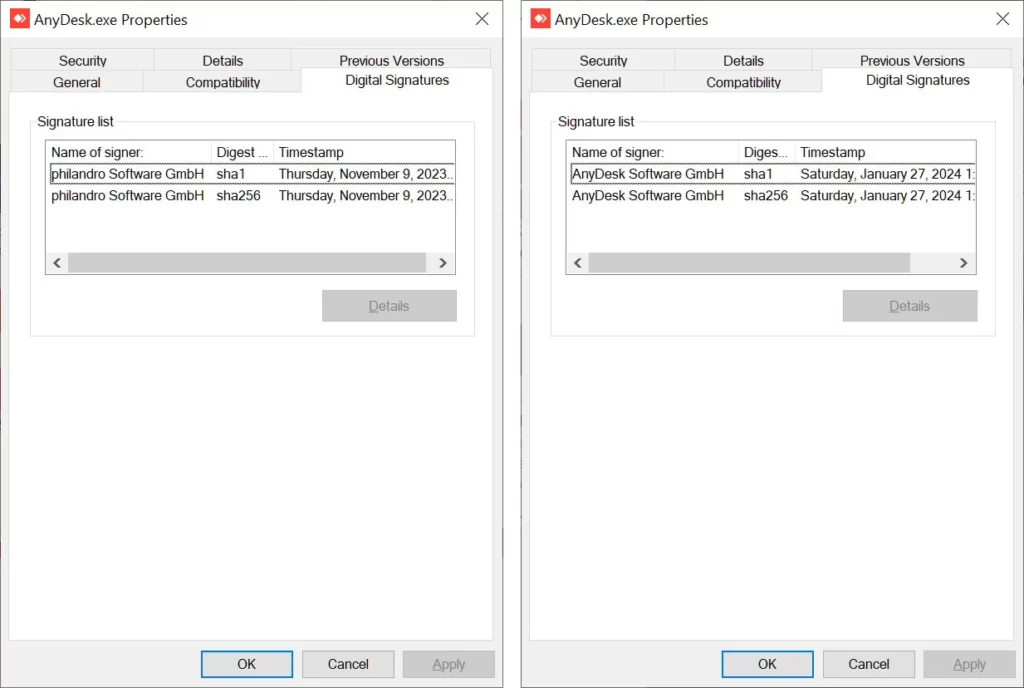
The latest update, released on January 29th, marks a crucial step in AnyDesk’s efforts to mitigate the risks posed by the breach. With the new code signing certificate in place, users can benefit from enhanced security measures designed to safeguard their remote access sessions.
Following the breach, AnyDesk has remained transparent about the incident, promptly informing users about the compromise and advising them on necessary precautions. Despite the reassurance that authentication tokens were not stolen, AnyDesk is proactively revoking all passwords to their web portal as a precautionary measure.
Moreover, the company’s decision to replace stolen code signing certificates underscores its commitment to maintaining the integrity of its software ecosystem. By promptly addressing the security vulnerabilities exposed by the breach, AnyDesk aims to restore user confidence and ensure the continued safety of its platform.


