In this technology-driven world, people are more inclined towards the use of advanced forms of technology. It is a boon in disguise in the lives of people using technology in amalgamation with technique. Apart from industrialization, the IT industry has been continuously evolving. All the works in our lives nowadays are getting inspiration from the latest computational methods. In a way, technological advancement is making our lives easier, but on the other hand, security is an issue here. Computational technologies are rapidly evolving in all spheres of life. Amidst all these security breaches has put a mark of tension on the foreheads of many experts. Many sectors are presently working on cybersecurity to provide a hassle-free service of intrusion detection and prevention systems to business clients.
Some Light on the Fact of Intrusion Detection and Prevention
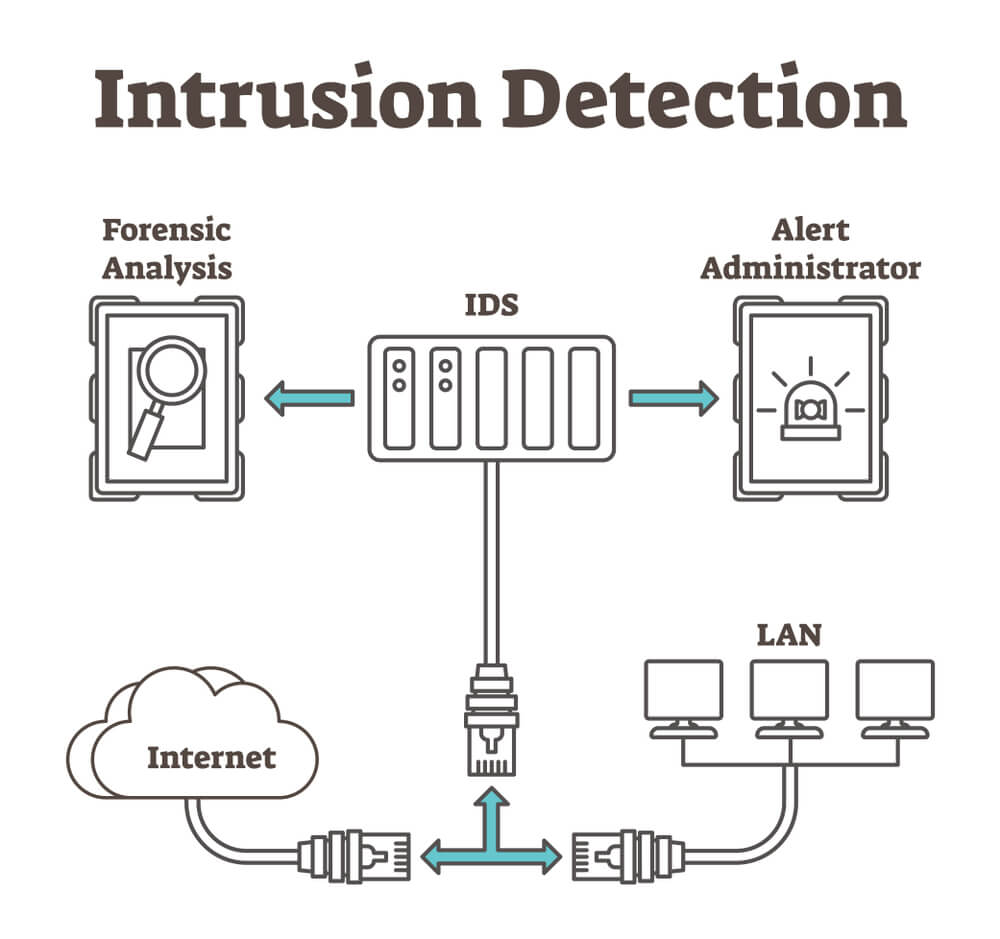
The intrusion detection system is an integral part of the surveillance system. It works to manage and protect the privacy of the digital data of business customers. It forms a core part of the cybersecurity department. An intrusion system is a system that detects and identifies any suspicious activity over the road of the network. It works to clear off the network traffic in the business and also retain a secure network system in the business. The intrusion system is a collection of effective software that successfully identifies a network breach on the network. It also devises ways to combat such issues of policy breaching.
There is a separate centralized security management system or a central administrator who gets detailed information of any violation activity. He then passes them down to the central administrator. The security administrator will receive updates regarding the presence of malicious activities in the network. There is tallying information from data from multiple sources occurs. Post the indication the intrusion software draws a fine line of difference between the occurrence of malicious threats and false alarms.
Some Categories of Intrusion Detection System
- There is a network intrusion detection system that has a central operational mode that is the strategic point in the network. This network intrusion system can monitor the traffic from all other devices that are associated with the network. The system performs an analysis of the traffic present on the entire subnet. It matches the known traffic present on the network server to that passing into the library. The library can prove as a source of known attacks. After the match analysis occurs, the network intrusion detection system can detect prospective attacks on the network library. It is strong enough to send an alert signal to the administrator instantly. You can install a network intrusion detection system on the subnet where the firewalls are already present. It will help to detect any malicious attack that can try to break the firewall. Checking and scanning all the inbound and outbound traffic on the server is essential for the administrator. However, it can lead to unnecessary traffic on the system and slow down the network operations. The network intrusion detection system can store, scan, and match the signatures of the network packages. It can detect the presence of any unauthorized network packet with a similar signature. The interaction of the traffic on the sub-server can be on-line and offline. The on-line mode handles the network traffic and its intrusion system on a real-time basis while the offline system analyzes the data in storage already followed by which it passes the data down to some process to decide the nature of the attack.
- There is an intrusion detection-driven artificial neural network that is capable of handling large data set effectively. It is due to the organized structure of the artificial neural network. The mode of operations of the advanced artificial neural network can recognize the attacks more efficiently. It works in a two-layer process. The first layer takes the single value inputs and the second layer takes the results from the first set as their inputs and categorizes the malicious attacks as per the automatic unidentified attacks on the system.
- Then there is the host intrusion detection system that operates on the individual server host system. The system analyzes both the inbound and outbound network packets from the individual server host device and will notify the administrator about any suspicious attack. This system has a unique code of operations. The specific software takes the screenshot of the previous customer files and data and matches them with the present data. If any data goes missing, it will automatically update the administrator about the probable malicious attack.By alerting the administrator, the host-based intrusion detection system speeds up the process of figuring out the cause of the attack so that it is thwarted. A host-based intrusion detection system, according to Liquid Web, not only shields against malicious attacks, but also protects networks from asymmetric routing, buffer overflow attacks, and scanning attacks, which could lead to DDoS attacks, remote code execution, and viruses.
Advantages of Intrusion Detection System
In-depth Monitoring of the Network System-
If a business organization makes up its mind for installing the intrusion detection system, they will derive many benefits from them. The intrusion system will help the organization to monitor the exact functioning of the firewall cybersecurity. It will also help monitor the functioning of the key files and servers using the signature depository database. It enables easy detection of malicious attacks.
Fewer Anomalies-
There is a low risk of false-positive cases in the case of intrusion system. The nature of the system is much organized and, there are fewer anomalies associated with raising alarms for malicious attacks. Effective signature detection methods reduce the occurrence of misleading alarms.
All Round Detection-
The intrusion system serves a dual function. It analyzes the specific malicious attacks on the network. If it detects such anomaly, it also identifies the accurate contents of the attack. It will also help the authority to have more effective control over the security of the business organization.
There are many advantages of the Intrusion Prevention System. The intrusion prevention system manages the security issues in the business by raising alarms. It is to indicate an attack on the network. In addition to it, the intrusion prevention system can also modify the contents in the areas of framing rules and regulations.
SSL technology encrypts ongoing information from data spying and data theft. You can choose SSL from different types of SSL certificates like single domain, multi domain, cheap wildcard SSL, code signing certificate etc. Always prefer budget SSL.
This intrusion prevention system will prevent attacks on a specific host that operates according to SSL technology. It is your responsibility to choose the best intrusion prevention system to maintain the privacy of your organization.